 |
| Add caption |
Constantly testing software and tinkering with a variety of Linux operating systems puts my multiple test-bench computers to constant use. Granted, Linux comes with a lot fewer security risks. But dealing with unknown factors and beta glitches can be time consuming to correct when they take down an entire box.
A much safer and quicker way to deal with such potential harm is to spare the physical machines and run the new stuff in a virtual machine instead. Oracle's (Nasdaq: ORCL) VM VirtualBox 4.0 is a handy app for doing just that. It runs nicely in a variety of Linux distros.
Oracle's VM software is not the only choice for running other OSes inside a particular Linux distro. But it is one of the easiest solutions. For example, you can install Parallels, Qemu, KVM (Kernel's Virtualization Machine) and VMWare.
These options are not an equal fit. Each one has its own strengths and weaknesses. But if your goal is to run something else without having to shut down your currently running OS and dual boot or turn on a second computer, VirtualBox is a very solid option to choose.
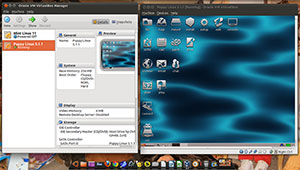
Virtual Info
VirtualBox runs on both x86 and AMD64/Intel64 systems and is suitable for enterprise or home use. Enterprise users will appreciate its feature-rich, high-quality performance. Home users will recognize its simplicity to use without poring over documentation.
Besides being Linux-friendly, Oracle's VirtualBox runs on Windows, Macintosh and Solaris hosts and supports a large number of guest operating systems including, but not limited to, Windows (NT 4.0, 2000, XP, Server 2003, Vista, Windows 7), DOS/Windows 3.x, Linux (2.4 and 2.6), Solaris and OpenSolaris, OS/2, and OpenBSD.
It is a general-purpose full virtualizer that targets server, desktop and embedded use. VirtualBox 4.0.8 was released on May 16 as a maintenance upgrade. Version 4.0, released last December, was a big step forward in adding features to VirtualBox.
The current 4.0 line introduced a two-fold product distribution to better address user needs. The base package is a fully functional release. Extension Packs add further feature refinements that provide more specialized solutions.
Download and Get Going
I have used earlier versions of VirtualBox on other versions of the Ubuntu Linux OS. I put this latest version through its paces on Ubuntu 11.04 running the classic rather than Unity desktop option.
Normally, I install software packages through the Ubuntu Software Center when it is available. VM VirtualBox is available through Ubuntu's repository.
But I wanted to ensure that I had the latest version, so I downloaded the .deb package from the the virtualbox.org wiki site noted above. Not having to unarchive the package or compile it was much appreciated. It installed through the package manager with no issues.
The Setup Scenario
Much like using word processors or spreadsheets, virtual machine apps are very similar in their look and feel. You follow the same basic process to run a VM app within a host OS.
For instance, you first have to create the virtual environment and set certain parameters. The virtual machine must share processor and memory resources with the host.
If you over-tax the VM app, the host's performance suffers. The goal is to be able to run programs or processes within the isolated VM environment while still being able to run the host's applications. So it becomes a balancing act.
After setting up the virtual machine to run inside the physical computer, you then install one or more OSes to run inside the VM. VirtualBox does this very handily by suing two separate wizards.
Get Started
The setup process is very straightforward with VirtualBox. Once you have the first run process completed, all you have to do is run the app and click on your installed options. Here is how it works.
First, press the New button in the main tool bar at the upper left of the VirtualBox window. This loads the New Virtual Machine Wizard. Then press the Next button at the bottom of the window.
Now enter a name for the VM session and select the OS Type from the drop-down windows. The choices are MS Windows, Linux, Solaris, BSD, IBM (NYSE: IBM) OS/2, Mac OS X or other.
Next, select the amount of base memory (RAM) in megabytes you want to allocate to the virtual machine. The recommended amount is 256MB, which is the default setting on the slide bar. Then click Next.
Finally, select the type of Virtual Hard Disk the virtual machine will use as the boot hard disk. You have two choices: create a new one or use an existing one. The default is create new. Then click Next again.
Moving On
The second part of the first use process is creating the virtual disk on your physical system. The VirtualBox window now displays the Create New Virtual Disk Wizard window. Start it by clicking the Next button.
Now you need to decide on the hard disk storage type. Again, you have two choices.
The default is dynamically expanding storage. This lets the VM machine start out with a small storage area on the physical hard drive and expand it as needed.
The other choice is a fixed-rate storage. This is a finite amount of storage stored. It consumes about the same size as the size of the virtual hard disk.
Be careful here. The creation of a fixed-sized storage can take a long time depending on the storage size and the write performance of your hard disk. You can click the Back button or Next button to continue.
Almost There
Next comes setting the Virtual Disk location and size. The Location window shows the name you already entered for the current VM session. You can change it or click the file manager-like button to select the desired location.
Next you must use the sliding scale to set the virtual hard disk size in megabytes. This size will be reported to the Guest OS as the maximum size of this hard disk. When ready, click the Back or Next buttons.
Carefully view the summary window. If you want to make changes, click the Back button. Otherwise, click the Finish button. A second summary window appears. Almost instantly, the VirtualBox Manager window replaces the previous summary window.
How to Use It
The first use setup is now finished. All that remains to be done is putting the guest OS in the virtual machine.
To start this installation, put the installation medium in the drive or find out its storage location on the physical hard drive. Then click the New button in the VM VirtualBox Manager window.
Follow the prompts. The process repeats the steps of the second wizard above.
To run the VM installation, click on the Guest OS label in the left panel of the VirtualBox Manager. The guest OS will run in its own self-contained sandbox window on the desktop. When you are finished, you can suspend the VM status to resume in a next session or quit that session.
Meanwhile, the host environment returns to full resource capabilities once you exit the Virtual application. This sure is better than having to interrupt what you are doing in the host Linux desktop so you can reboot/dualboot the system two or three times.




















